Reimplementation of a Collaborative Threat Modeling Tool
[This topic is currently reserved] Threat modeling is a structured process to identify potential threat sources and the events they may cause on an information system. As such, they aim to help answer the question of “what could go wrong?” and not necessarily “what is wrong in the system?” (vulnerabilities). This distinction is important for cases where vulnerability assessment is not feasible, realistic, or cost-efficient [1].
Currently, many threat modeling approaches and applications exist [2]. However, they are either inflexible, closed-source, or they require specific input data [3]. Thus, this thesis requires reimplementing an existing open-source, diagram-based threat modeling tool. More specifically, this thesis requires that a wrapper for diagrams.net is implemented to provide basic automation and guidance of the "STRIDE per interaction" methodology [1].
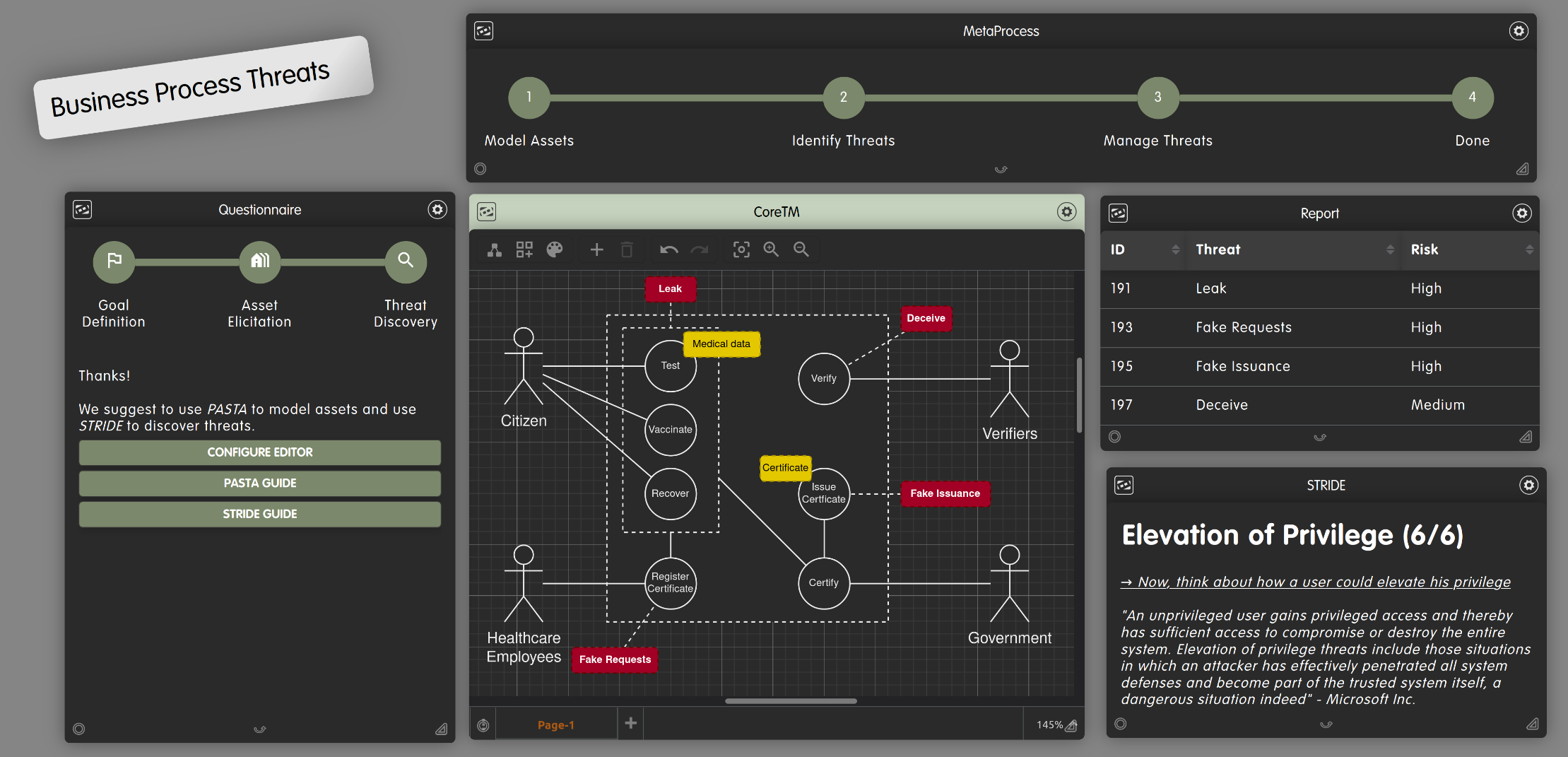 Fig.1 - Creating a Threat Model of a Use Case with CoReTM
Fig.1 - Creating a Threat Model of a Use Case with CoReTM
This thesis is supervised in combination with an industrial partner, allowing for extensive knowledge transfer from cybersecurity professionals applying threat modeling in their daily business. While this work requires experience in web development, it does not require knowledge in cybersecurity. Thus, this could be an excellent segway for a student interested in exploring cybersecurity as a career path or simply exploring this topic.
[1] A. Shostack, "Threat modeling: Designing for security," John Wiley & Sons, 2014.
[2] O. A. Aslan, R. Samet, “A Comprehensive Review on Malware Detection Approaches,” IEEE Access, vol. 8, pp. 6249–6271, 2020
[3] J. von der Assen, M. F. Franco, C. Killer, E. J. Scheid, B. Stiller: "CoReTM: An Approach Enabling Cross-Functional Collaborative Threat Modeling," IEEE International Conference on Cyber Security and Resilience, Virtually, Europe, July 2022, pp. 1–8. Available Online
Supervisors: Jan von der Assen
back to the main page